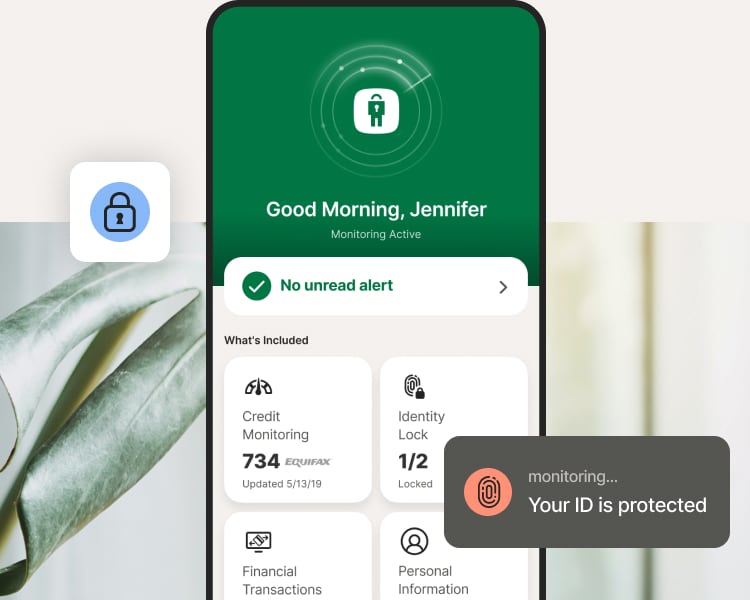
Guard against identity theft and help keep your finances safe.
Get comprehensive identity protection for the ultimate peace of mind.
 Call us
Call us
Get comprehensive identity protection for the ultimate peace of mind.
Finances
Restoration
Personal info

Finances
We go above and beyond to keep your money safe, monitor for identity theft in places that banks, credit card providers, and credit bureaus may ignore, and reimburse out-of-pocket expenses incurred as a result of identity theft.

Restoration
Our industry-leading U.S.-Based Personal Restoration Specialists restore your identity. And with our most comprehensive plan, our Million Dollar ProtectionTM Package reimburses stolen funds and covers personal expenses, each with limits of up to $1 million, and covers Lawyers and Experts, if needed, up to $1 million.†††

Personal info
We help keep your personal information private and out of the hands of people trying to steal your money or commit crimes in your name. Plus, we alert you when we find your personal information exposed on the dark web and in places other services may miss.
There's a victim of identity theft in the U.S. every 3 seconds.**
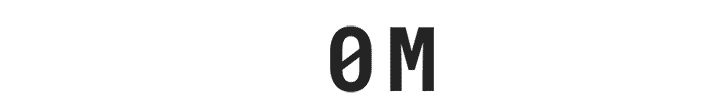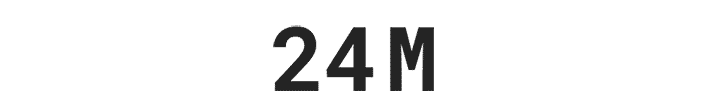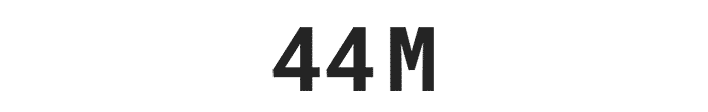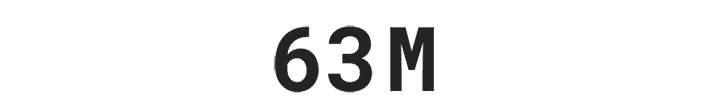
More than 63 million Americans have been affected by identity theft.
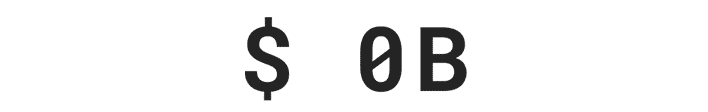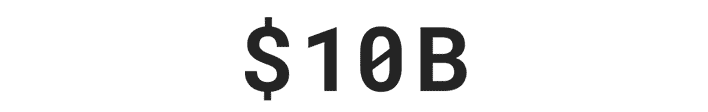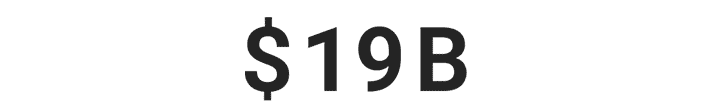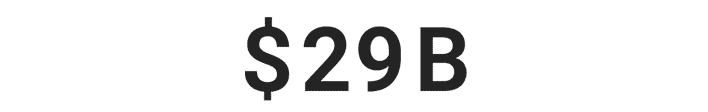
Over $29 billion was stolen by identity thieves in 2022.***
Want more protection?
Add device security and VPN for all-in-one protection.
Let us do the work so you can focus on what matters most.
Over $29 billion was stolen by identity thieves in 2022.***
*** Based on an online survey of 505 U.S. adults who experienced ID theft in 2022, conducted for Gen™ (formerly NortonLifeLock) by The Harris Poll, January 2023.
More than 63 million Americans have been affected by identity theft.**
** Based on an online survey of 5,004 adults in the U.S. conducted by The Harris Poll on behalf of Gen™ (formerly NortonLifeLock), January 2023.
Million Dollar Protection™ Package†††
Million Dollar Protection™ Package†††
Million Dollar Protection™ Package†††
Million Dollar Protection™ Package†††
Million Dollar Protection™ Package†††
Million Dollar Protection™ Package†††
Million Dollar Protection™ Package†††
Million Dollar Protection™ Package†††
Million Dollar Protection™ Package†††
401(k) & Investment Alerts†
Social Media Monitoring
Bank & Credit Card Activity Alerts†
Credit Scores & Credit Reports
Buy Now Pay Later Alerts
Recurring and Unusual Charge Alerts
Credit Monitoring Coverage3
Dark Web Monitoring
Stolen Funds Reimbursement†††
Lawyers & Experts†††
††† Up to $1 million for coverage for lawyers and experts included on all plans. Reimbursement and Expense Compensation varies according to plan, up to $1 million each for LifeLock Ultimate Plus.
Insurance benefits are issued by third parties.
See NortonLifelock.com/Legal for policy info.
† LifeLock does not monitor all transactions at all businesses.
3 Credit features require successful setup, identity verification, and sufficient credit history by the appropriate credit bureau. Credit monitoring features may take several days to activate after enrollment.
Identifying your concerns gives us the ability to recommend the right plan for your needs.
Knowing this number helps us recommend coverage that fits your needs.
Providing your email address makes you eligible for notifications of potential identity threats.

"The 600-pound gorilla in the ID Protection space, LifeLock has one of the most comprehensive services for preventing an identity theft and if that fails, surviving it."

LifeLock stood out for the simplicity and ease of use of its mobile app.1
No one can prevent all cybercrime or prevent all identity theft.
††† Up to $1 million for coverage for Lawyers and Experts included on all plans. Reimbursement and expense compensation varies according to plan—up to $1 million each for LifeLock Ultimate Plus. Insurance benefits are issued by third parties. See GenDigital.com/legal for policy info.
1 Javelin Strategy & Research’s 2022 Identity Protection Service Provider Scorecard.
3 Credit features require successful setup, identity verification, and sufficient credit history by the appropriate credit bureau. Credit monitoring features may take several days to activate after enrollment.
12 Identity Lock cannot prevent all account takeovers, unauthorized account openings, or credit file inquiries. Deactivates if you downgrade or cancel your subscription.
† LifeLock does not monitor all transactions at all businesses.
** Based on an online survey of 5,004 adults in the U.S. conducted by The Harris Poll on behalf of Gen™ (formerly NortonLifeLock), January 2023.
*** Based on an online survey of 505 U.S. adults who experienced ID theft in 2022, conducted for Gen™ (formerly NortonLifeLock) by The Harris Poll, January 2023.
Copyright © 2024 Gen Digital Inc. All rights reserved. All trademarks, service marks, and tradenames (collectively, the "Marks") are trademarks or registered trademarks of Gen Digital Inc. or its affiliates ("Gen") or other respective owners that have granted Gen the right to use such Marks. For a list of Gen Marks please see GenDigital.com/trademarks.